We are in the process of curating a list of this year’s publications — including links to social media, lab websites, and supplemental material. Currently, we have 68 full papers, 23 LBWs, three Journal papers, one alt.chi paper, two SIG, two Case Studies, one Interactivity, one Student Game Competition, and we lead three workshops. One paper received a best paper award and 13 papers received an honorable mention.
Disclaimer: This list is not complete yet; the DOIs might not be working yet.
Your publication from 2025 is missing? Please enter the details in this Google Forms and send us an email that you added a publication: contact@germanhci.de
A Qualitative Study of Adoption Barriers and Challenges for Passwordless Authentication in German Public Administrations
Jan-Ulrich Holtgrave (CISPA Helmholtz Center for Information Security), Sabrina Klivan (CISPA Helmholtz Center for Information Security), Karola Marky (Ruhr University Bochum, Bochum), Sascha Fahl (CISPA Helmholtz Center for Information Security)
Abstract | Tags: Full Paper, Security | Links:
@inproceedings{Holtgrave2025QualitativeStudy,
title = {A Qualitative Study of Adoption Barriers and Challenges for Passwordless Authentication in German Public Administrations},
author = {Jan-Ulrich Holtgrave (CISPA Helmholtz Center for Information Security), Sabrina Klivan (CISPA Helmholtz Center for Information Security), Karola Marky (Ruhr University Bochum, Bochum), Sascha Fahl (CISPA Helmholtz Center for Information Security)},
url = {https://teamusec.de/, website},
doi = {10.1145/3706598.3713252},
year = {2025},
date = {2025-04-26},
urldate = {2025-04-26},
abstract = {Public administrations provide critical services and manage sensitive data for a country's citizens. Recent phishing campaigns targeting public sector employees highlight their attractiveness as targets. Deploying state-of-the-art authentication technologies, such as FIDO2, can improve overall security. We conducted a mixed-methods study in Germany to understand better the practices and challenges of deploying passwordless authentication in the public sector. First, we conducted an online survey (N=108) among German public sector employees to gain insights into their experiences and challenges. Next, we partnered with an e-government vendor and performed an in-situ experiment. We let 11 employees from the public sector experience FIDO2 under real-world conditions. Our results show that only a minority of our participants were aware of current passwordless authentication procedures. In our experiment, FIDO2-based methods left an overall positive impression. Hierarchical and heterogeneous public sector structures and the need for more technical expertise and equipment were barriers to adoption.},
keywords = {Full Paper, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Cyber Threat Awareness, Protective Measures and Communication Preferences in Germany: Implications from Three Representative Surveys (2021-2024)
Marc-André Kaufhold (PEASEC, TU Darmstadt), Julian Bäumler (PEASEC, TU Darmstadt), Marius Bajorski (PEASEC, TU Darmstadt), Christian Reuter (PEASEC, TU Darmstadt)
Abstract | Tags: Full Paper, Security | Links:
@inproceedings{Kaufhold2025CyberThreat,
title = {Cyber Threat Awareness, Protective Measures and Communication Preferences in Germany: Implications from Three Representative Surveys (2021-2024)},
author = {Marc-André Kaufhold (PEASEC, TU Darmstadt), Julian Bäumler (PEASEC, TU Darmstadt), Marius Bajorski (PEASEC, TU Darmstadt), Christian Reuter (PEASEC, TU Darmstadt)},
url = {https://peasec.de/, website
https://www.linkedin.com/company/peasecde/, linkedin
https://bsky.app/profile/peasec.de, bsky},
doi = {10.1145/3706598.3713795},
year = {2025},
date = {2025-04-26},
urldate = {2025-04-26},
abstract = {In light of the increasing vulnerability of citizens against cyberattacks, we conducted three representative surveys with German citizens in 2021 (N=1,093), 2023 (N=1,011), and 2024 (N=1,004) to examine their cyber threat awareness, use of protective security measures, and preferred information channels. While our findings attest large proportions of the German population a high level of cyber threat awareness, many citizens feel inadequately informed about coping with cyberattacks and show little confidence in German security authorities to protect citizens and infrastructures. While age correlated with citizens' awareness and behavior, we only saw minor temporal differences between datasets. Finally, we provide design and policy implications for enhancing citizens' awareness of cyber threats and implementing security measures.},
keywords = {Full Paper, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
Exploring the Effect of Music on User Typing and Identification through Keystroke Dynamics
Lukas Mecke (LMU Munich, University of the Bundeswehr Munich), Assem Mamoud ( German University in Cairo), Simon Marat (LMU Munich), Florian Alt (LMU Munich, University of the Bundeswehr Munich)
Abstract | Tags: Full Paper, Security | Links:
@inproceedings{Mecke2025ExploringEffect,
title = {Exploring the Effect of Music on User Typing and Identification through Keystroke Dynamics},
author = {Lukas Mecke (LMU Munich, University of the Bundeswehr Munich), Assem Mamoud ( German University in Cairo), Simon Marat (LMU Munich), Florian Alt (LMU Munich, University of the Bundeswehr Munich)},
doi = {10.1145/3706598.3713222},
year = {2025},
date = {2025-04-26},
urldate = {2025-04-26},
abstract = {This paper explores the relationship between music and keyboard typing behavior. In particular, we focus on how it affects keystroke-based authentication systems. To this end, we conducted an online experiment (N=43), where participants were asked to replicate paragraphs of text while listening to music at varying tempos and loudness levels across two sessions. Our findings reveal that listening to music leads to more errors and faster typing if the music is fast. Identification through a biometric model was improved when music was played either during its training or testing. This hints at the potential of music for increasing identification performance and a tradeoff between this benefit and user distraction. Overall, our research sheds light on typing behavior and introduces music as a subtle and effective tool to influence user typing behavior in the context of keystroke-based authentication.},
keywords = {Full Paper, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
The Illusion of Privacy: Investigating User Misperceptions in Browser Tracking Protection
Maximiliane Windl (LMU Munich), Roman Amberg (LMU Munich), Thomas Kosch (HU Berlin)
Abstract | Tags: Full Paper, Security | Links:
@inproceedings{Windl2025IllusionPrivacy,
title = {The Illusion of Privacy: Investigating User Misperceptions in Browser Tracking Protection},
author = {Maximiliane Windl (LMU Munich), Roman Amberg (LMU Munich), Thomas Kosch (HU Berlin)},
url = {https://www.medien.ifi.lmu.de/index.xhtml.en, website
https://www.linkedin.com/company/lmu-media-informatics-group, research group linkedin
https://www.linkedin.com/in/maximiliane-windl/, author's linkedin},
doi = {10.1145/3706598.3713912},
year = {2025},
date = {2025-04-26},
urldate = {2025-04-26},
abstract = {Third parties track users' web browsing activities, raising privacy concerns. Tracking protection extensions prevent this, but their influence on privacy protection beliefs shaped by narratives remains uncertain. This paper investigates users' misperception of tracking protection offered by browser plugins. Our study explores how different narratives influence users' perceived privacy protection by examining three tracking protection extension narratives: no protection, functional protection, and a placebo. In a study (N=36), participants evaluated their anticipated protection during a hotel booking process, influenced by the narrative about the plugin's functionality. However, participants viewed the same website without tracking protection adaptations. We show that users feel more protected when informed they use a functional or placebo extension, compared to no protection. Our findings highlight the deceptive nature of misleading privacy tools, emphasizing the need for greater transparency to prevent users from a false sense of protection, as such misleading tools negatively affect user study results.},
keywords = {Full Paper, Security},
pubstate = {published},
tppubtype = {inproceedings}
}
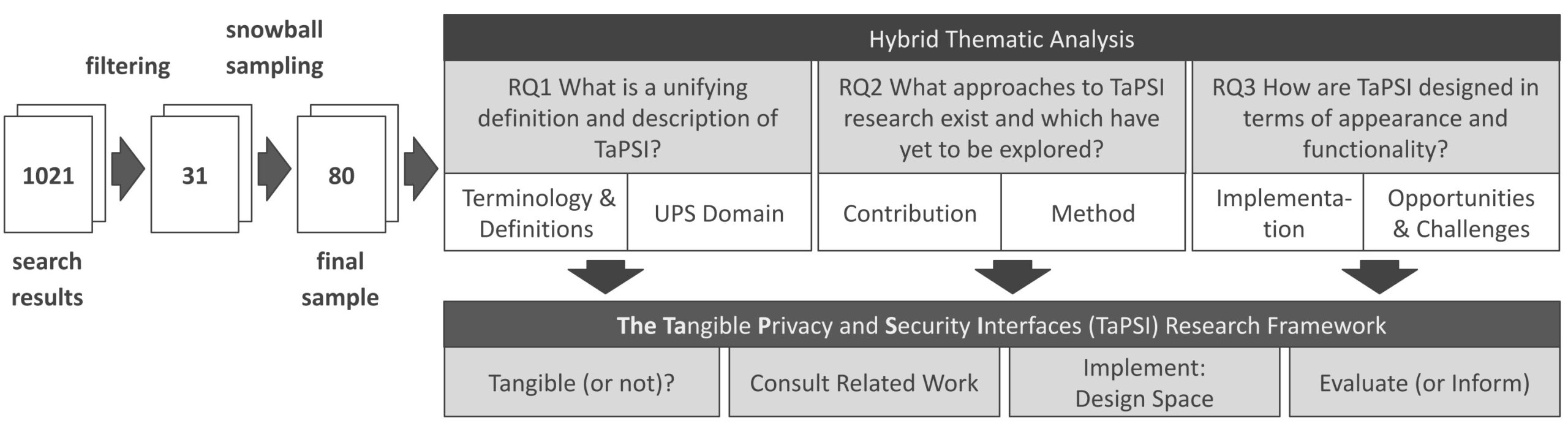
The TaPSI Research Framework - A Systematization of Knowledge on Tangible Privacy and Security Interfaces
Sarah Delgado Rodriguez (University of the Bundeswehr Munich), Maximiliane Windl (LMU Munich), Florian Alt (LMU Munich, University of the Bundeswehr Munich), Karola Marky (Ruhr University Bochum)
Abstract | Tags: Full Paper, Security | Links:
@inproceedings{Rodriguez2025TapsiResearch,
title = {The TaPSI Research Framework - A Systematization of Knowledge on Tangible Privacy and Security Interfaces},
author = {Sarah Delgado Rodriguez (University of the Bundeswehr Munich), Maximiliane Windl (LMU Munich), Florian Alt (LMU Munich and University of the Bundeswehr Munich), Karola Marky (Ruhr University Bochum)},
url = {https://www.medien.ifi.lmu.de/, website
https://www.linkedin.com/company/lmu-media-informatics-group/, research group linkedin
https://www.linkedin.com/in/sarah-delgado-rodriguez-9b9573270?utm_source=share&utm_campaign=share_via&utm_content=profile&utm_medium=android_app, author's linkedin
https://www.instagram.com/mediagroup.lmu?igsh=djd6ZWNpbGN1ajF0, instagram},
doi = {10.1145/3706598.3713968},
year = {2025},
date = {2025-04-26},
urldate = {2025-04-26},
abstract = {This paper presents a comprehensive Systematization of Knowledge on tangible privacy and security interfaces (TaPSI). Tangible interfaces provide physical forms for digital interactions. They can offer significant benefits for privacy and security applications by making complex and abstract security concepts more intuitive, comprehensible, and engaging. Through a literature survey, we collected and analyzed 80 publications. We identified terminology used in these publications, addressed usable privacy and security domains, contributions, applied methods, implementation details, and opportunities or challenges inherent to TaPSI. Based on our findings, we define TaPSI and propose the TaPSI research framework, which guides future research by offering insights into when and how to conduct research on privacy and security involving TaPSI as well as a design space of TaPSI.},
keywords = {Full Paper, Security},
pubstate = {published},
tppubtype = {inproceedings}
}